Rethinking Digital Sovereignty – From Decentralized Control to a “Cloud NATO” for Europe
Cloud infrastructure has quietly become one of the most strategic layers of modern sovereignty. The ability to store, process, and control data within national or regional boundaries isn’t just a regulatory preference anymore. It’s a matter of economic security, political leverage, and systemic resilience.
Across Europe, the pressure is mounting to find alternatives to centralized cloud dependencies, especially on non-European hyperscalers. But the response doesn’t have to be isolation or reinvention. A new kind of architecture is emerging, one that combines local control with collective strength.
This article explores two major ideas driving the conversation forward: decentralized digital sovereignty and the potential for a NATO-style model of cloud governance. It also looks at how Oracle Cloud aligns with this vision as a modular enabler of sovereignty, interoperability, and trust.
The Shift Toward Decentralized Sovereignty
When digital sovereignty first entered the mainstream conversation, it was often framed in binary terms: own the stack, or remain dependent. Control your cloud, or get locked in. But real-world infrastructure isn’t built on such clean lines. Across Europe, what’s emerging is a decentralized approach to sovereignty – one that accepts technical diversity, regulatory pluralism, and federated execution.
A decentralized model doesn’t reject sovereignty, it redefines it. Each country, or even each sector, can set and enforce its own policies around data protection, infrastructure, and compliance. But instead of operating in isolation, these systems connect through shared governance, open standards, and secure interoperability. It’s not about building a pan-European hyperscaler but about creating a European cloud ecosystem.
This is the principle behind initiatives like Gaia‑X, which doesn’t aim to replace existing infrastructure, but rather to standardize how participants exchange data, certify services, and establish trust. It’s sovereignty is maintained at the edge, but coordinated at the core.
This model is particularly well-suited to the European context, where data protection laws like the GDPR already offer a common legal framework, but where political and operational control must remain localized. Sovereignty, in this sense, becomes a set of enforceable guarantees, not a monolithic stack.
From Decentralization to Collective Defense – A “Cloud NATO”?
Decentralized control brings autonomy, but what about defense? In a digital world, resilience isn’t just about uptime. It’s about coordination. Europe needs to think beyond who hosts the data and start asking how we defend, recover, and coordinate our digital responses as a unified front.
The idea of a “Cloud NATO” is more than a metaphor. Like its military counterpart, it would be built on the principle of shared responsibility with local autonomy. Each country would operate its own cloud environment: certified, secured, and governed by its own rules. But all participants would align on common protocols for interoperability, auditing, security standards, and incident response.
Think of it as a federation of sovereign clouds: decentralized in ownership, but unified in execution when needed. Such a model would preserve the diversity of national approaches and offer a collective backbone for coordination and trust.
In moments of crisis, whether regulatory, technical, or geopolitical, a NATO-style alliance would allow sovereign clouds to mutually support each other, share threat intelligence, and even mirror critical workloads across trusted jurisdictions. In a time of rising cyber threats, digital fragmentation is not an option, but neither is centralization. A federated alliance may be the only workable path.
Where Oracle Cloud Fits In
To make these models viable, Europe needs cloud providers that don’t force one mode of operation. It needs platforms that support sovereignty by design, federation by architecture, and trust by default. Oracle Cloud brings several elements to this table.
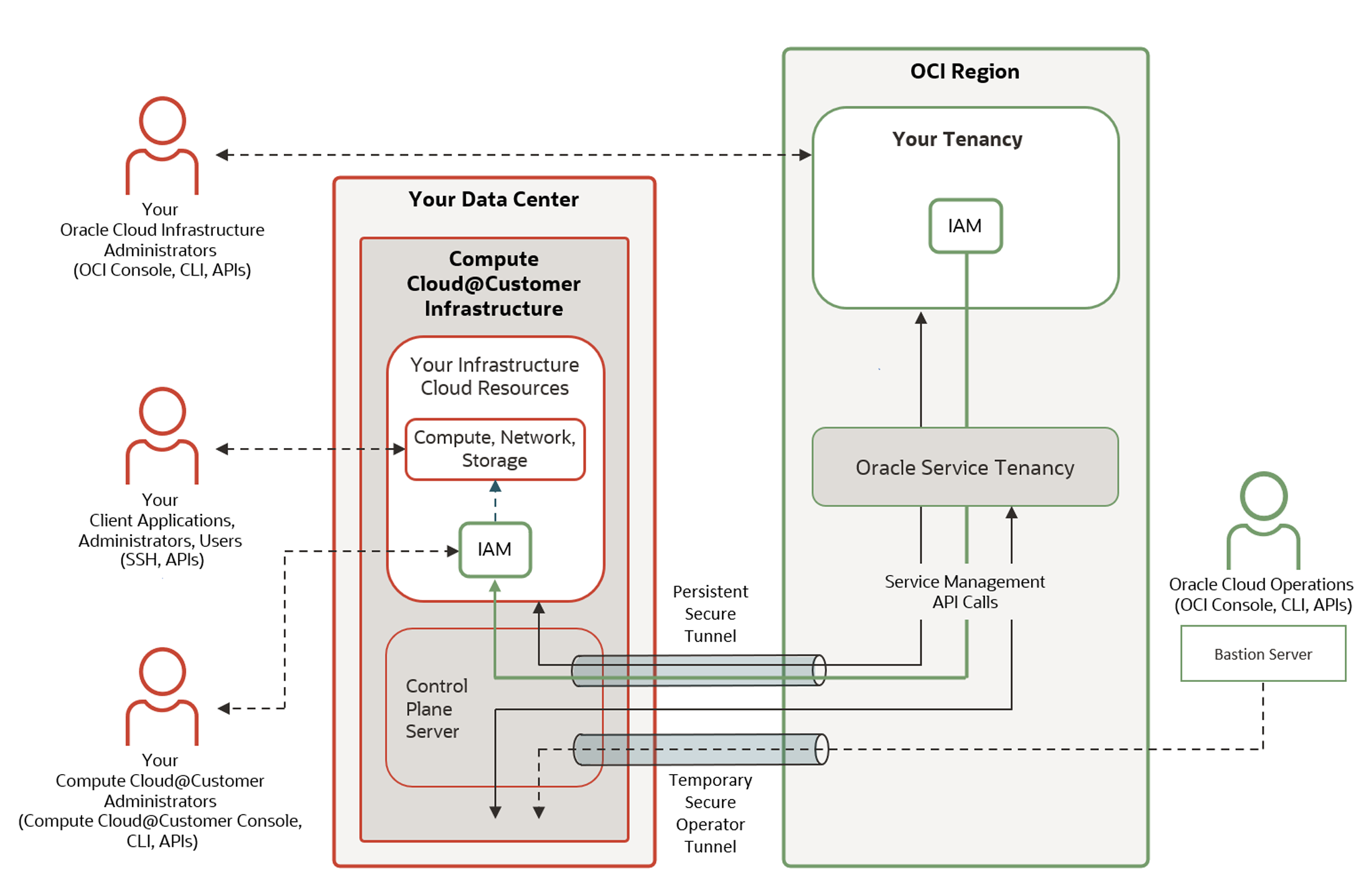
Oracle offers one of the most modular and flexible cloud deployment models in the hyperscaler landscape. With Dedicated Region and Cloud@Customer, Oracle enables governments and critical industries to deploy full-featured Oracle Cloud environments within national borders or sovereign facilities. That means local control over infrastructure, compliance, and operations- without giving up cloud-native scalability or modern service architectures.
Crucially, Oracle’s architecture emphasizes openness. It supports Kubernetes, open APIs, and multi-cloud integrations, ensuring sovereign environments aren’t isolated silos but nodes in a larger ecosystem. Whether connecting ministries across borders or bridging data domains between sectors, this openness makes decentralized coordination feasible at scale.
Building Blocks for a “Cloud NATO”
For a federated governance model to work, interoperability isn’t enough. Providers must support auditable governance, strong identity management, transparent encryption controls, and legal separation of sovereign workloads. Oracle’s EU Sovereign Cloud does exactly that: operating independently from its global infrastructure, with EU-based support, operations, and compliance.
Oracle also demonstrates multi-cloud execution through its partnership with Microsoft Azure, Amazon Web Services and Google Cloud, where Oracle Database services run natively in Azure, AWS or GCP data centers. It’s a working example of what a trusted, cross-platform alliance can look like. Tech giants respect the sovereignty of each other’s platforms while delivering real interoperability.
These technical capabilities are supported by a broader strategy: Oracle doesn’t push for lock-in or exclusive dependencies. It supports coexistence and federation. The very principles that would make a “Cloud NATO” not just possible, but resilient.
Sovereignty Is Evolving. So Should the Cloud
The old model of sovereignty – one state, one data center, one stack – is no longer viable. Europe needs an approach to cloud that is both locally governed and globally coordinated.
Decentralized sovereignty gives each country the autonomy it needs. A “Cloud NATO” gives the continent the collective strength it lacks. Together, they offer a roadmap not just for compliance, but for cloud independence with integrity.
And for this to work, cloud providers must be more than platforms, they must be partners in sovereignty. Oracle’s architecture, deployment flexibility, and governance tooling place it in a unique position to support this shift. Not by dominating the stack, but by enabling distributed trust.
The future of Europe’s cloud may not belong to a single player. It may belong to an alliance.